Cybersecurity
Secure what matters most -
identities, applications, and data

Threat Detection and Responses
Implement a holistic security framework to identify, protect, detect, respond and recover from cybersecurity threats.
FLYER
Reduce Your Exposure Time
WHITE PAPER
OpenText™ Enterprise Security Analytics with an Audit Quality SIEM Solution
PRODUCT OVERVIEW
OpenText™ Core Adversary Signals
Why accurate insider threat detection relies on measuring "unique normal", and how unsupervised machine learning plays a critical role.

Threat Detection and Responses
Implement a holistic security framework to identify, protect, detect, respond and recover from cybersecurity threats.
FLYER
Reduce Your Exposure Time
WHITE PAPER
OpenText™ Enterprise Security Analytics with an Audit Quality SIEM Solution
PRODUCT OVERVIEW
OpenText™ Core Adversary Signals
Why accurate insider threat detection relies on measuring "unique normal", and how unsupervised machine learning plays a critical role.

Seamless App Security
Secure your applications and protect your business with the most comprehensive, accurate and scalable application security solution that works with your DevSecOps processes
BROCHURE
Fortify Overview
FLYER
Fortify and Sonatype Deliver
99% reduction in time spent reviewing and approving OSS components.

Seamless App Security
Secure your applications and protect your business with the most comprehensive, accurate and scalable application security solution that works with your DevSecOps processes
BROCHURE
Fortify Overview
FLYER
Fortify and Sonatype Deliver
99% reduction in time spent reviewing and approving OSS components.

Data Protection
Discover and classify sensitive data to manage risk; protect data and enforce identity-based access for applications and users; and comply with privacy mandates with confidence and trust.
WHITE PAPER
SecureData Cloud & Analytics
DATASHEET
Data Privacy & Protection Foundation
Learn how to secure cloud analytics and how your organization can stay secure and compliant in the cloud.

Data Protection
Discover and classify sensitive data to manage risk; protect data and enforce identity-based access for applications and users; and comply with privacy mandates with confidence and trust.
WHITE PAPER
SecureData Cloud & Analytics
DATASHEET
Data Privacy & Protection Foundation
Learn how to secure cloud analytics and how your organization can stay secure and compliant in the cloud.
Risk and Compliance Management
Orchestrated vulnerability risk and IT compliance management for the hybrid enterprise
SOLUTION OVERVIEW
The Role Discovery and CMDB Play in Compliance and Security
DATASHEET
Automation Center
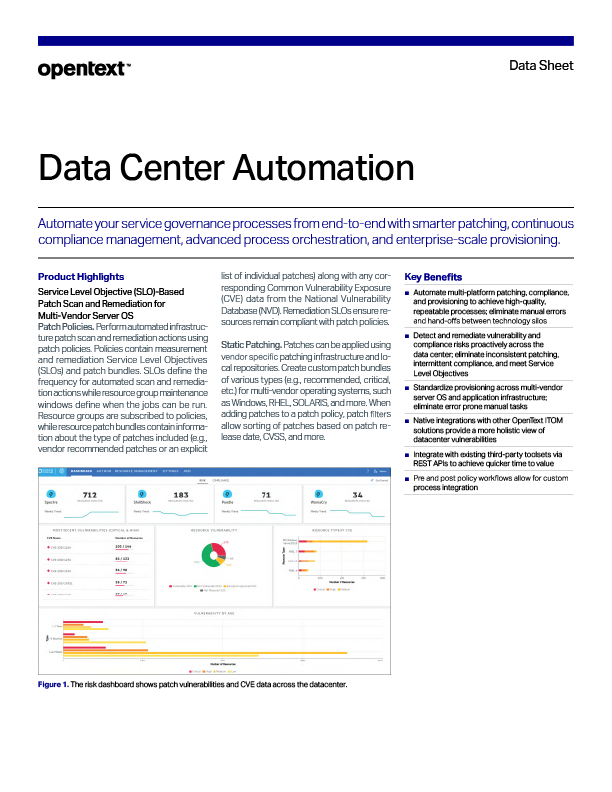
See how *OpenText™ Automation Center helps IT Operations teams accelerate their vulnerability remediation.
Risk and Compliance Management
Orchestrated vulnerability risk and IT compliance management for the hybrid enterprise
SOLUTION OVERVIEW
The Role Discovery and CMDB Play in Compliance and Security
DATASHEET
Automation Center
See how *OpenText™ Automation Center helps IT Operations teams accelerate their vulnerability remediation.

Identity and Access Management
Mitigate security risk by ensuring only authorized users access sensitive data. Use robust authentication to reduce data breaches and enable real-time threat response.
PRODUCT OVERVIEW
OpenText™ Identity Governance
FLYER
OpenText™ Advanced Authentication for Your Business
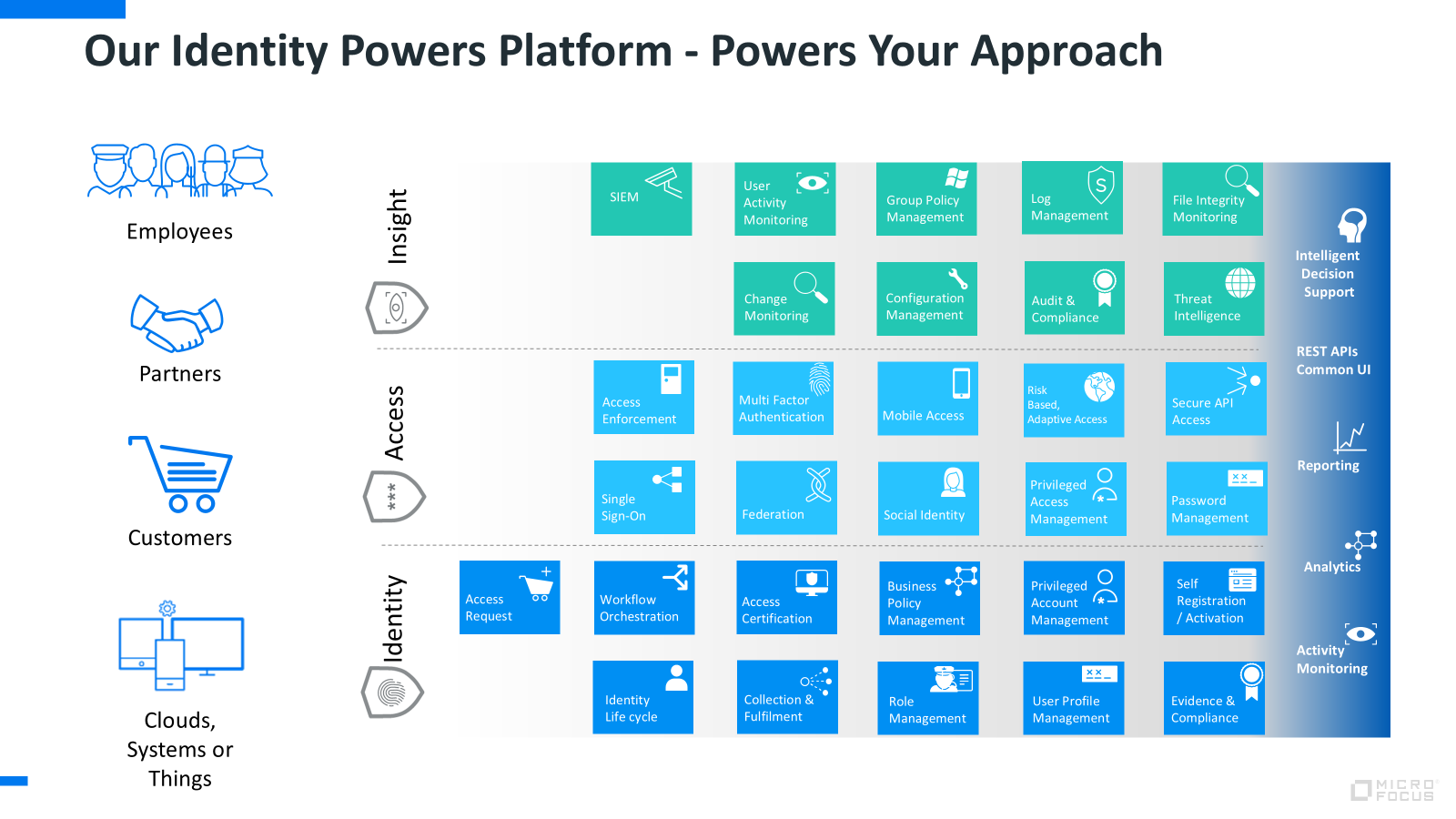
Seamlessly control who has access to what without compromising user experience or compliance.

Identity and Access Management
Mitigate security risk by ensuring only authorized users access sensitive data. Use robust authentication to reduce data breaches and enable real-time threat response.
PRODUCT OVERVIEW
OpenText™ Identity Governance
FLYER
OpenText™ Advanced Authentication for Your Business

Seamlessly control who has access to what without compromising user experience or compliance.